Explain the Different Types of Authentication Methods
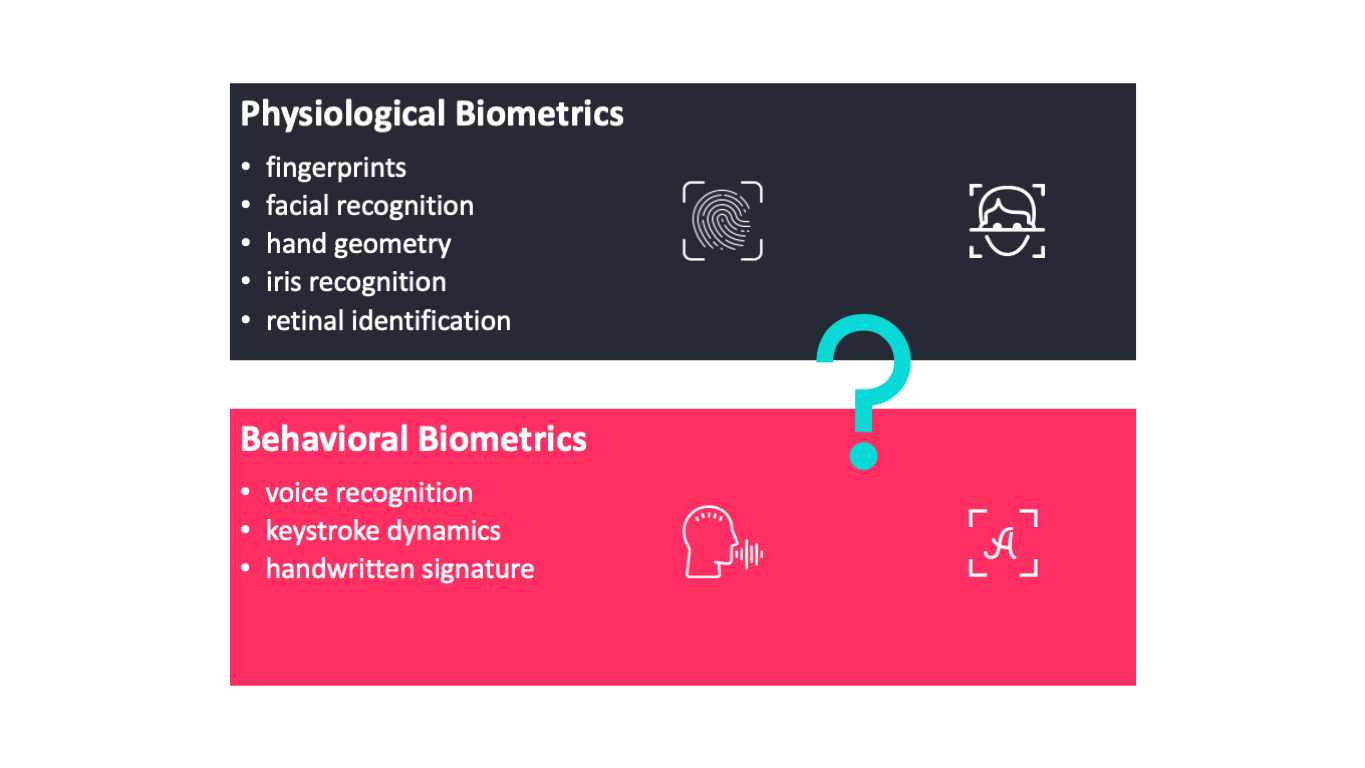
There are a number of authentication methods that can be used to confirm the identity of users who connect to. Two perform biometric authentication two techniques are used physiological techniques and behavioral techniques.

What Is Clickjacking In This Article We Will Look At The Different Types Of Clickjacking Attacks And Reveal To You The Most I Techniques Threat Prevention
It requires the password for the particular username.
. Explain the difference between refutable and irrefutable authentication providing an example of both types in your answer. It is the simplest way of authentication. 5 Common Authentication Types 1.
However you cant disable the password authentication method. A user enters the username and password then both the server and the client generates a one-time password. Authentication using symmetric keys-Suppose two users share a symmetric key K and this key is only known to both.
Use this guide to determine which makes the most sense for your application. Physiological technique makes use of face fingerprint voice retina Iris. Multi-Factor Authentication MFA is an authentication method that requires two or more.
In process of authentication the key K must not be revealed to a third party user. Identification phase provides a user identity to the security system. These methods are used in applications that leverage two-factor authentication.
There are various ways a user can be authenticated - some of which include Session-based authentication Cookie-based authentication Token-based authentication Claims-based authentication and HyperText Transfer Protocol HTTP authentication mechanisms. The selection of the most appropriate type of authentication will depend on the needs of the application. In behavioral technique persons behavior is observed to ensure that he or she is not trying to claim to be someone else.
Authentication using public keys-. Authentication process can be described in two distinct phases - identification and actual authentication. Time-based One-time Password Algorithm based on the current time HMAC-based One-time Password Algorithm based on a counter.
If the password matches with the username and both details match the systems database the user will be. As far as authentication is concerned there are mainly three types of WLAN authentication methods that are used today. Passwords can be in the form.
An Azure AD password is one of the primary authentication methods. Like 2FA MFA uses factors like biometrics device-based confirmation additional passwords and even location or behavior-based information eg keystroke pattern or typing speed to confirm user identity. Three categories in which someone may be authenticated are.
6 points Define what the term authentication means and specify three different types of authentication methods 4 points SSLTLS is considered best practice for securing web sites. There are many different types of authentication that can be used in an application. Passwords are the most common methods of authentication.
There are various methods available for primary or secondary authentication lets start with the first one that is Password. The various methods are. Multi-factor authentication is a high-assurance method as it uses more system-irrelevant factors to legitimize users.
Something the user knows something the user is and something the user has. Authentication can be accomplished by proving knowledge of this shared symmetric key.
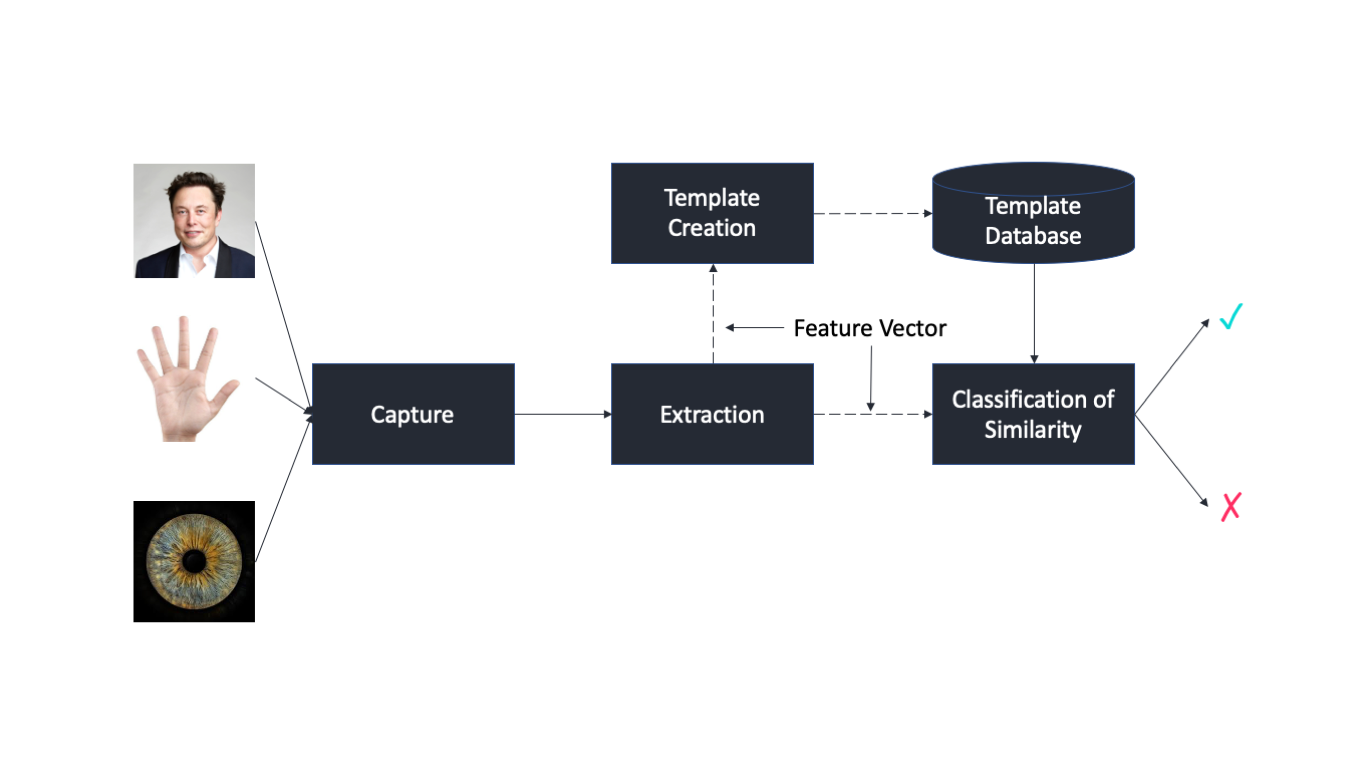
Biometric Authentication Methods Fingerprints Facial Recognition Hand By Anh T Dang Towards Data Science

User Authentication Methods Technologies To Prevent Breach

What Is Passwordless Authentication Benefits Of It Method Does It Work Understanding

User Authentication Methods Technologies To Prevent Breach

User Authentication Methods Technologies To Prevent Breach

Authentication Method An Overview Sciencedirect Topics
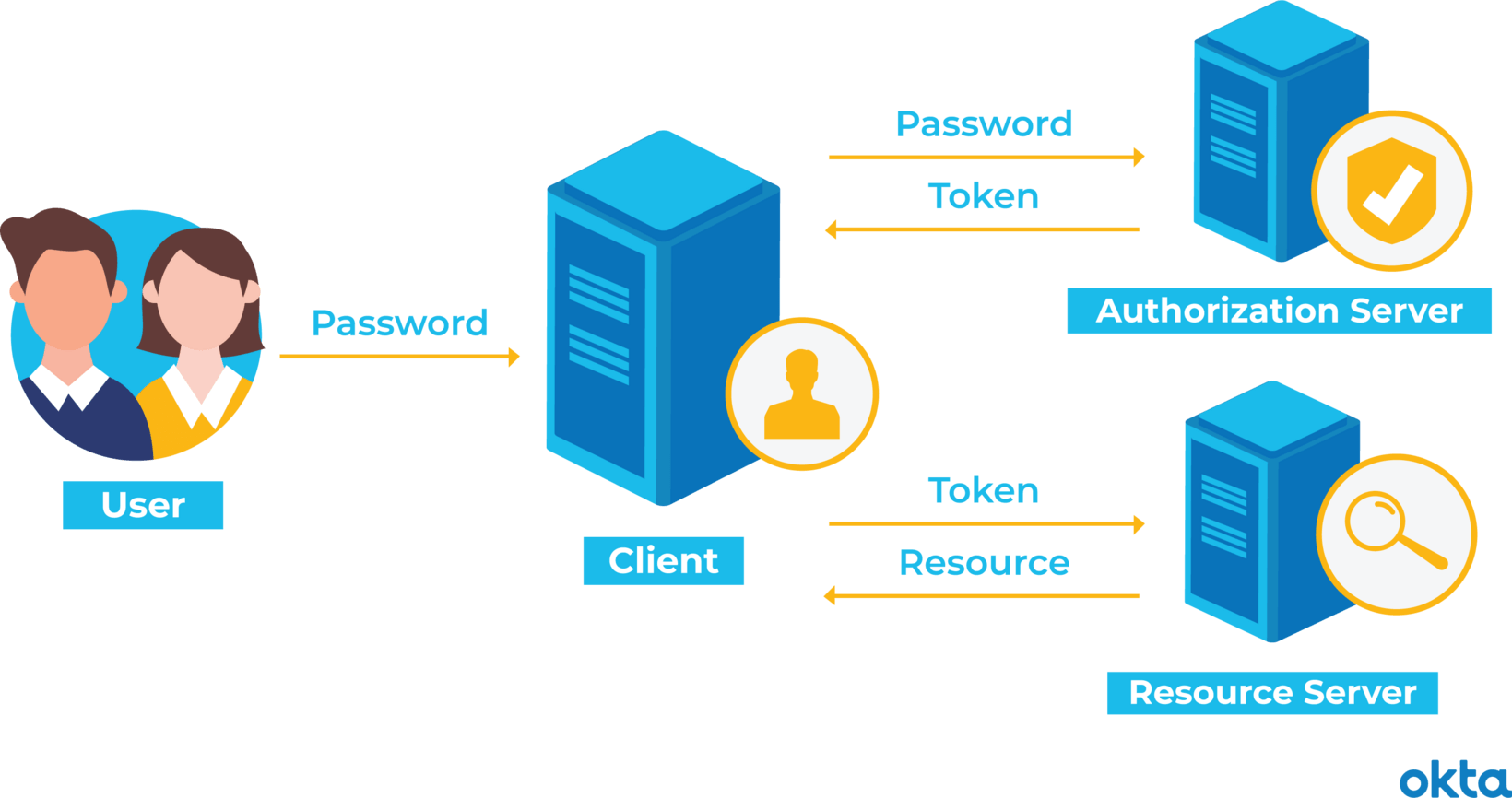
What Is Token Based Authentication Okta

User Authentication Methods Technologies To Prevent Breach

Biometric Authentication Methods Fingerprints Facial Recognition Hand By Anh T Dang Towards Data Science

Mike Amundsen On Linkedin 4 Api Authentication Methods To Better Protect Data In Transit In 2022 Network Security Ibm Networking

Authentication Method An Overview Sciencedirect Topics

What Is Open System Authentication Osa

Authentication Vulnerabilities Web Security Academy

What Is Sap Analytics Cloud Tunnel Connection Configure Sac Hana To Use Tunnel Connection With Password Authentication Sap Connection Clouds
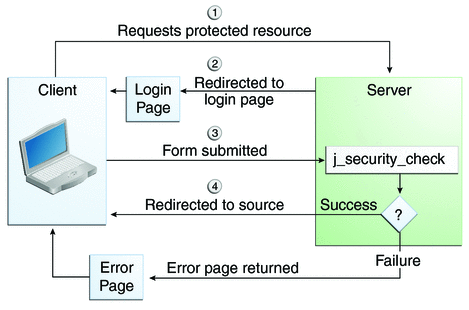
Form Based Authentication The Java Ee 6 Tutorial

Authentication Method An Overview Sciencedirect Topics


Comments
Post a Comment